Dr. Allison Fish and Professor Brad Sherman
I. Introduction
Information regulation law and theory tends to focus on the role law plays in regulating technologies that generate, collect, manipulate, or use data and, in so doing, generate insights about the world. In these situations, the role of law is to mediate and temper the excesses of information technology that were unanticipated in their design and deployment. This might include, for example, how the law can be used to allay privacy concerns relating to novel surveillance systems or how the law might be used to realign discriminatory bias built into algorithmic decision-making tools. The prevailing discourses embedded in these accounts frames social concerns and the related legal responses as something that is brought about after the release of technologies into the ‘wild’, as a means to rectify any unanticipated problems that arise, or in order to increase the transparency of the ‘black box’ surrounding automated decision making.[1]
Importantly, in these dominant narratives, law is not only conceptualised as being external to various information systems, it is also placed temporally in a position where it invariably lags behind technology development and usage. In this context, the relationship between law and technology is overwhelmingly one-sided: it is one in which rapid technological innovation constantly outpaces and evades the glacial development of legal reform. Scholars working in this vein envision a world in which technological innovation gallops ahead and, in the process, changes our social realities and alters our legal ‘common sense’. Moreover, this disjunct between our changing socio-technical worlds and stagnant legal imaginaries creates a gap that renders visible the inability of modern democratic laws to deliver on its promises of transparency, procedural and substantive justice, and social equality. The argument continues that valuable social goods such as the rule of law and techno-scientific progress, quite literally hinge upon the resolution of this gap. Here, the role of law is to catch up with and attempt to make good the problems created by technological change.[2] While many early works on this topic focused on the ways copyright stifled access to the knowledge commons in the early days of the digital revolution, this argument has been extended to other domains, including the regulation of data privacy and surveillance, FinTech, social media and fake news, and labour in the platform economy.[3]
While there is much to learn from this approach, we wish to take a different line of inquiry in this paper. Instead of looking at law as something that is external to information technology development and deployment, we analyse a situation where the legal-regulatory apparatus is embedded within the information system itself. To do this, we examine a case study involving the Indian state’s development and use of a technological system to meeting its international obligation to monitor compliance under the Nagoya Protocol, an international legal instrument regulating the movement of genetic resources and associated knowledge. Specifically, we look at the bespoke machine learning tool that has been developed in India that uses data science approaches to monitor the use of Nagoya protected resources: the IT Monitoring Tool for Access and Benefit Sharing. We then explore the lessons that this case study offers for information regulation law and theory.
It is our argument that there are numerous aspects of the Indian state’s approach to dealing with its obligations under the Nagoya Protocol that are important for information regulation law and theory. One of the most significant is that it represents a situation where instead of being an object of legal regulation, the information system itself has become a tool of legal regulation. In this sense the Indian approach to implementing and monitoring compliance under the Nagoya Protocol emerges as an unusual example of ‘compliance through design’: that is, where legal regulatory goals are interpreted and actioned via a technological infrastructure composed of both heritage and novel tools.[4]
II. The Operation of the Nagoya Protocol
The techno-legal knowledge infrastructure that interests us here grew out of the fact that over the last half century, the international legal frameworks regulating genetic resources[5] have changed dramatically. A key reason for this was the signing of the Convention on Biological Diversity (“CBD”) in 1992 which introduced the legal principle that States have sovereignty over the genetic resources located within their borders. This was in marked contrast to the situation previously where genetic resources were considered to be the ‘common heritage’ of humankind and freely available for use without restriction.[6] The CBD has three aims – to promote the conservation of biodiversity, the sustainable use of biodiversity, and the fair and equitable sharing of the benefits arising from the utilisation of genetic resources and associated (‘traditional’) knowledge. While the first two objectives have been relatively uncontroversial, there has been little agreement with respect to the third.
The push towards a more fair and equitable sharing of benefits under the CBD took an important turn when the Nagoya Protocol was adopted in October 2012.[7] The Protocol provides Member States with guidance on how the CBD is to be implemented and reaffirms the sovereign rights of States over their natural resources. The primary objective of the Nagoya Protocol is to ensure the fair and equitable sharing of benefits arising from the utilisation of the genetic resources and any associated knowledge.[8]
To ensure the fair and equitable sharing of benefits, the Nagoya Protocol aims to establish a standardised framework that allows potential users to access and utilise genetic resources.[9] It also aims to ensure that any benefits that arise from the utilization of genetic resources are shared fairly and equitably with providers. The Protocol does this by requiring Member States to adopt measures that ensure that users obtain prior informed consent from the providers of biological material before they access genetic resources; and that there are benefit sharing agreements in place between users and providers of biological material. The framework is intended to provide greater legal certainty and transparency for both providers and users of these resources. It also aims to ensure that providers receive some of the benefits that arise from the use that is made of their genetic resources.
Unlike many international legal agreements which only apply in the country where they are enacted, the Nagoya Protocol also regulates behaviour outside of the countries where it has been adopted into national law. This is because countries that have ratified the Protocol are not only under an obligation to ensure that the genetic resources used in the country are Nagoya complaint, they are also under an obligation to ensure that the biological material imported into the country was collected, used, and/or developed in compliance with the Protocol. Specifically, they are required to ensure that biological material imported into the country is accompanied by relevant documentary evidence including: access permits from the relevant authorities; prior informed consent from authorities and providers of biological material; and benefit sharing agreements between users and providers of biological material. As a result, the Protocol applies to people who want to export material into a country that has implemented the Nagoya Protocol. This means, for example, that a company in the United States (which is not a member of the CBD let alone a signatory to Nagoya) that wants to export biological material to India (which has adopted Nagoya), will only be able to do so if they can show that the biological material is ‘Nagoya compliant’.
The global reach of the Nagoya Protocol has also been extended by the fact that a growing number of non-State institutions, such as universities, herbaria, and scientific journals have made Nagoya compliance a pre-condition of dealing with biological materials. For example, even though the United States is neither a party to the CBD nor a signatory to the Protocol, the University of California (or at least parts thereof) has nonetheless decided that it will adopt Nagoya as best practice when dealing with biological resources.[10] This means that for a researcher in Australia (which has signed but not yet implemented Nagoya) to export a plant to a colleague at the University of California, they would need to be able to show that the plant was Nagoya compliant. In a similar vein, a growing number of scientific publications, such as the suite of Nature journals, require contributors writing about biological material to make the underlying research materials available to readers without restriction or to show that the biological resources studied were collected with all necessary approvals (BMC journals).[11]
Another innovative feature of the Nagoya Protocol is the online platform known as the Access and Benefit Sharing (“ABS”) Clearing House.[12] The clearing house is intended to function as an informational tool for enhancing legal certainty, clarity, and transparency regarding compliance and monitoring of the Nagoya Protocol. To accomplish this, the clearing house allows provider countries to publicise who has been authorised to utilise genetic resources and for what purposes.[13] The primary mechanism for publicising this information is the Internationally Registered Certificates of Compliance (“IRCCs”) which are tracked through a centralised database. IRCCs are publicly available on the clearing house website and are generated when the appropriate representative from the provider country, the National Publishing Authority, enters the relevant information into the clearing house.[14] In this sense, the IRCCs act as an internationally accepted template for providing evidence that a user has complied with the provider country’s ABS rules.
The IRCCs listed on the clearing house website flag the Indian state’s importance in establishing global best practice in the implementation of the Nagoya Protocol. Significantly, at the close of 2020, 22 Member States had lodged approximately 2000 IRCCs. Of this number, 1330 certificates (more than 65%) had been filed by India.[15] In understanding the dominance of the Indian state’s use of the clearing house’s IRCC feature, we refer to recent work on the explanatory power of quantitative indicators in global governance.[16] This emerging body of work tends to focus on how quantitative indicators of legal governance are produced, disseminated, and used in a manner that reduces complex social phenomena and relationships into simple, quantifiable, and ranked terms. The overriding presumption is that these ‘simple to read’ indicators of global governance are shaped by experts in the Global North and are mobilised to measure the rule of law (or lack thereof) in the Global South. A closer look at how the Indian state has dominated use of the IRCC mechanism belies an interesting twist on this presumption about the dynamics of global governance. In doing so, India emerges as a site of global standard-setting, decision-making, and contestation over whether and how soft international law, like the Nagoya Protocol, can be enforced. An analysis of how this has been achieved first requires an understanding of the domestic implementation of the Nagoya Protocol in India.
III. The Implementation of the Nagoya Protocol in India
A. Creating a Pathway to Bioprospecting: Authorised Access and Publicising Compliance
While India only has 2.4% of the world’s land area, it accounts for 7-8% of all recorded species, including over 45,000 species of plants and 91,000 species of animals.[17] Given this, it is not surprising that managing the access and use of genetic resources and associated knowledges in an appropriate manner is an important consideration for the Indian central government.[18] In line with this, India signed the CBD in 1992.[19] As part of the state’s obligations under this instrument, India implemented the Biological Diversity Act in 2002. The National Biodiversity Authority was established shortly thereafter in 2003 as an autonomous statutory body under the Ministry of Environment, Forestry and Climate Change to implement the provisions and coordinate the national-level response. Thus, when India ratified the Nagoya Protocol in late 2012, becoming the fifth country to do so, the National Biodiversity Authority became the body through which the country’s obligations were executed. A press release issued shortly after ratification noted that as a megadiverse country, India
“had been a victim of misappropriation, or biopiracy, of our genetic resources and associated traditional knowledge, which have been patented in other countries (well- known examples include neem and haldi) … and it is expected that the ABS Protocol is a key missing pillar of the CBD [that] would address this concern”.[20]
In implementing the Nagoya Protocol, and in pursuit of the prevention of biopiracy, the Indian strategy operates across three tiers of government:
- A single National Biodiversity Authority, a central government agency headquartered in Chennai,[21]
- State Biodiversity Boards and Union Territory Councils in each state or territory,[22] and
- Approximately 270,000 Biodiversity Management Committees that operate at the level of the local community.[23]
With respect to meeting the country’s obligations under the Nagoya Protocol, the National Biodiversity Authority is responsible for coordinating across all three tiers of government and providing support to state and local entities.[24] In addition, the national authority manages the permit system for all foreigners using Nagoya protected resources, the transfer of research results to foreign entities, and any intellectual property claims related to Nagoya-protected resources.[25]
In describing the mammoth task facing the National Biodiversity Authority, the chairman, Dr. Vinod Mathur, said
“it was when we started implementing [the Nagoya Protocol] that we realized that there were major gaps and we started asking how information technology could help us in plugging this gap and that is perhaps the origin of … the role of IT in the kind of monitoring tool that we have tried to develop.” [26]
According to Mathur, the first step was to use technology to create a single, centralized point which private parties interested in commercial and non-commercial bioprospecting activities in India could use to obtain authorizations from central, state, and local bodies. To do this, the National Biodiversity Authority created the ABS e-filing system, an online portal which is used to lodge bioprospecting applications that detail information such as the resource that would be utilized, the purpose of use (e.g., commercial or non-commercial), and area of use (e.g., pharmaceutical, agricultural, etc). After lodging an application, the request is referred to the relevant State Biodiversity Board, the entities charged with mediating access and benefit sharing agreements with relevant local Biodiversity Management Committees.[27] The resulting benefit sharing agreement is then attached to the application and the whole package is reviewed by expert panels, the relevant State Board(s), and the National Biodiversity Authority. Once all relevant approvals are received, the National Biodiversity Authority will authorise the application in the ABS e-filing system and a permit will be issued. This automatically triggers the Indian National Publishing Authority to file an IRCC in the CBD’s ABS Clearing House system.[28] While most countries only provide IRCCs in their own domestic language, in order to enhance their global accessibility, the certificates published by India are provided in all official United Nations’ languages.[29]
The Indian scheme, which allows for the coordinated review of applications, results in a single decision about authorisation, thus avoiding the problem of applicants obtaining permits at some levels of government, but not others. It also provides a mechanism by which approved bioprospecting activities are domestically and internationally publicised. To do this, the Indian state had to create an entirely new regulatory structure to track the movement of bioprospecting decisions across the three-tiers of this administrative hierarchy via a centralized ABS e-filing system. Though fairly straightforward in concept, recent evaluations of the novel ABS e-filing system indicate there are still several practical problems that need to be resolved.[30] Despite these barriers, in creating this centralized system the National Biodiversity Authority operates both conceptually and literally as the ultimate arbiter of decisions governing the use of Nagoya-protected resources in India. This reinforces the notion that while the management of biological and cultural resources should proceed according to local norms and state scrutiny, they are ultimately under the jurisdiction of the Indian central government and the province of national cultural patrimony. A notion that we argue is further reinforced outside of India and globally broadcast via the registration of IRCCs at the ABS Clearing House operated by the CBD.
B. Identifying and tracking biopiracy: Monitoring Non-Compliance Through Machine Learning
Having established a predictable and unified pathway for obtaining permits for the utilisation of Nagoya-protected resources (bioprospecting), National Biodiversity Authority officials turned their attention to the task of determining how the unauthorized utilisation of genetic resources (biopiracy) was to be monitored and policed. While some reports suggested that non-compliance was not a major issue,[31] more sustained research by Dr. Mukherjee, a scientist working at Deutsche Gesellschaft für Internationale Zusammenarbeit (“GIZ”) India, showed the depth of the problem. After studying the Indian access and benefit sharing scheme for four years and comparing this across patent applications filed in various jurisdictions around the world, Mukherjee concluded that only a ‘miniscule’ amount of benefit sharing was taking place in comparison to the vast amount of Indian-origin Nagoya-protected resources being used and exploited. According to Mukherjee, there were a number of contributing factors for this mismatch. The primary reason was that most users were outside of India and, therefore, outside the reach of the National Biodiversity Authority’s remit.[32] Another factor was that there was no easy way to monitor, identify, and police the misuse of Indian genetic resources and associated knowledge. Frustratingly, while many misuses were hiding in plain sight in publicly accessible scientific journals and patent applications, the sheer scale of these materials meant that searching, identifying, and tracing misuse was incredibly difficult and labour intensive.[33] As a result, Mukherjee and others working on the issue increasingly accepted that if the ABS scheme was to work effectively, the Indian state had to be able to monitor use and misuse of its Nagoya-protected resources. In thinking about how Nagoya compliance might be monitored, machine learning and data science approaches quickly emerged as a potential solution.
The task of building the computational tool for monitoring Nagoya compliance was undertaken by a public-private collaboration that included the National Biodiversity Authority, the Centre for Advanced Computing in Chennai (“C-DAC”), GIZ India, One World Analytics in London, as well as State Biodiversity Boards in Maharashtra, Tamil Nadu, and Uttarakhand. The resulting effort, IT Monitoring Tool, provides a means to identify when Indian Nagoya-protected resources are being used, assess whether those uses have received the appropriate approvals, and flag any suspicious cases for follow-up. The IT Monitoring Tool brings together a wider knowledge infrastructure involving pre-existing technologies and data repositories that are built upon legal and scientific classificatory systems.[34] Significantly, the wider knowledge infrastructure that is enabled by the IT Monitoring Tool monitors both the legitimate (bioprospecting) and illegitimate (biopiracy) use of Nagoya-protected resources.
To determine whether a Nagoya-protected resource of Indian origin has been used appropriately, the IT Monitoring Tool effectively asks a number of subsidiary questions. The most important of which are:
- Is there ‘use’ of a Nagoya-protected resource?[35]
- Does that use involve resources of Indian origin? and
- Has that use been ‘approved’ (or is it ABS compliant)?
In answering these questions, the IT Monitoring Tool draws upon a range of pre-existing online resources including a series of legacy databases, online information about scientific research and commercial use (both open access and subscription), and the National Biodiversity Authority’s ABS e-filing system. To monitor Nagoya compliance, the IT Monitoring Tool moves through a multi-step process. To determine whether the genetic resource has been ‘used’ in a way that falls within the scope of the Nagoya Protocol, the IT Monitoring Tool searches accessible locations of biodiversity-related research including patent filings in various jurisdictions, Web of Science, scientific publications, and other online resources such as Microsoft Access Graphs. This initial search, which involves a simple ‘yes’ or ‘no’ response to the question of whether biodiversity use has occurred, is complicated due to the scale of materials assessed including more than a billion taxonomic records, and hundreds of millions scientific publications and patent filings. With this done, the IT Monitoring Tool then evaluates the materials identified in the first step and assesses whether the biodiversity resources implicated might be of Indian origin and thus within Indian sovereign control. To make this assessment the IT Monitoring Tool draws upon pre-existing databases that contain relevant information about Nagoya-protected resources including the Botanical Survey of India, the Zoological Survey of India, the TKDL, and other collections that point to India as a possible ‘origin’ for the materials. Finally, to determine whether a use has been ‘approved’ (or is Nagoya compliant), the IT Monitoring Tool compares the findings of the previous two steps with information found within the National Biodiversity Authority’s ABS e-filing system which contains a list of authorised bioprospecting activities. If there are doubts about the legitimacy of the way the genetic resources are being used, the publication or patent is flagged for desk-review by an officer at the National Biodiversity Authority for attention. In this respect, the IT Monitoring Tool is not intended to operate as a fully autonomous decision-making system as it is anticipated that there is always a human-in-the-loop to render final judgment.
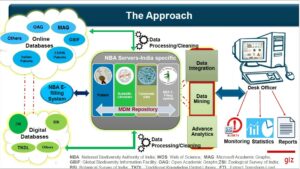
Figure 1: Diagram of IT Enabled ABS Monitoring System by Mukherjee A.[36]
The operation of the IT Monitoring Tool depends on the fact that patents, the scientific literature, the online and digital databases, the e-filing system, and the other aspects of the Nagoya-related knowledge infrastructure are all concerned in one way or another with specific genetic resources. It also depends on the fact that the genetic resources that are recorded in the digital repositories are not merely bare resources that have simply been plucked from nature and digitised. Rather, they are ‘informed materials’ which are constituted by the complex informational and material environments which they inhabit.[37] By the time a genetic resource is included in a patent application, the TKDL, a journal article, or a botanical or zoological collection, it will have already been evaluated, classified, and named. Importantly, while the different domains may require additional information to suit their specific needs, each database uses the same taxonomic and nomenclatural rules to categorise and describe the genetic resources. It is this shared language and grammar that allows the IT Monitoring Tool to monitor use across the different digital domains. The ability for the IT Monitoring Tool to move between databases is enhanced by the fact that the different classificatory systems have been designed to ensure that they do not unduly inhibit or restrict each other. Thus, for example, to promote scientific exchange, it is a longstanding legal rule that it is not possible to trade mark plant variety names, which are meant to be generic and freely available for everyone to use in a range of different contexts. This ensures that a scientific plant name can be used in the TKDL, in a journal publication, or in a patent application to refer to a specific biological entity. Similarly, scientific publications have long specified that when an author christens a biological object with a taxonomic name, they are unable to patent the type specimen used to ground the description and the name.
IV. The IT Monitoring Tool as the Most Recent Facet of a Techno-Legal Knowledge Infrastructure
A. Comparing TKDL and IT Monitoring Tool
The Indian approach to the Nagoya Protocol is part of a longer domestic history of using technological design to prevent the piracy of national biological and cultural patrimony that links back to the Traditional Knowledge Digital Library (“TKDL”). As a central government project, the TKDL was designed in direct response to a number of cases of perceived biopiracy that came to light in the 1980s and 1990s when patent offices in the United States and Europe approved claims relating to the wound-healing uses of turmeric, fungicidal and dental uses of neem, and on basmati rice stocks.[38] These claims led to a public outcry by Indian activists and governmental representatives who complained that foreign patent offices were permitting the privatisation of South Asian ethnobotanical knowledge.[39] As a result of these concerns, the Indian government challenged several of the offending patent claims during the 1990s. However, given the cost and the logistical difficulties involved in bringing patent challenges in foreign jurisdictions, coupled with the number of cases of suspected biopiracy of South Asian resources, there was also a desire for a more proactive and preventative approach.
This desire eventually resulted in the TKDL, an online database that was initiated in 2001 and developed under the auspices of the Councils of Scientific and Industrial Research in India in collaboration with the Indian System of Medicine and Homeopathy (entities that have been renamed the National Institute of Science Communication & Policy Research and Ministry of Ayurveda, Yoga, Unani, Siddha & Homeopathy, respectively).[40] The TKDL is explicitly designed to ‘fill the gaps in the law’ that allow biological and cultural piracy to take place and uses digitisation as a strategy to translate and render South Asian classical medical knowledge legible and available along three vectors – language, law, and science. To do this, the TKDL’s classificatory scheme mirrors that of the International Patent Classificatory system: a structure established and maintained by the World Intellectual Property Organization to organise and classify patents. Access to the TKDL is then granted to patent examiners in participating jurisdictions around the world to help them when assessing the novelty of patent applications.
Like the TKDL, the IT Monitoring Tool is a central government project designed to ‘fill the gaps’ in a legal system that allows unchecked biopiracy to take place. However, the TKDL and the IT Monitoring Tool have significant differences that cannot solely be attributed to technological sophistication. Firstly, the TKDL is designed to address problems associated with a narrow definition of biopiracy – inappropriate patent claims filed in relation to South Asian ethnobotanical knowledge. In contrast, the IT Monitoring Tool addresses a wider range of biopiracy activities – any unauthorised research or commercial activity involving South Asian biodiversity. A second distinction is that, in addition to tracking unauthorised or illegitimate uses of biodiversity, the IT Monitoring Tool can also track authorised utilisation or legitimate bioprospecting activities. Thirdly, as will be discussed below, the IT Monitoring Tool utilises a range of pre-existing databases (including the TKDL) as part of its operations. This utilisation reminds us that emerging techno-legal solutions are not always, or even regularly, built-for-purpose from the ground up. Rather, they often involve an aggregation and coordination of existing resources. As such, emerging solutions such as the IT Monitoring Tool may be constrained by the logics and structures of the heritage technologies that make up their component parts. Given this, as well as the ever-changing imagination and hype behind the TKDL, whether merited or not, India’s earlier experience with the use of technology to fill the gaps in the law may be instructive for understanding the future imaginations that will guide the IT Monitoring Tool.
Despite these differences, the TKDL provides an important basis of comparison to understand the IT Monitoring Tool for three reasons. Firstly, both tools, while aimed at resolving similar problems, are the product of experimental collaborations across different Indian central government ministries. On the one hand, the TKDL is the product of a collaboration between the National Institute of Science Information and Communication Resources, which sits within the Council of Scientific and Industrial Research, and the Ministry of Ayurveda, Yoga, Unani, Siddha and Homeopathy. In contrast, the IT Monitoring Tool involves a collaboration between the National Biodiversity Authority, which sits within the Ministry of Environment, Forests, and Climate Change, and the Centre for Development of Advanced Computing, which sits within the Ministry of Electronics and Information Technology. As a result, the two projects receive guidance on and are influenced by different ministries regulating similar domains – information technology and bio-cultural patrimony. However, both projects do receive some support and guidance from the Office of the Controller General of Patents, Designs and Trade Marks.
Secondly, both projects utilise a parallel approach to resolve a similar problem. Specifically, both the TKDL and the IT Monitoring Tool built and deployed bespoke computational technologies in an attempt to address the legal gaps that result in the inadequate regulation of bioprospecting and, as a result, allow biopiracy to occur. In this sense, neither the TKDL or the IT Monitoring Tool are projects aimed at pushing technological boundaries, but aim to resolve a similar problem. In order to achieve this resolution, both projects coordinate existing tools and layer these with novel computational approaches to arrive at a possible, even if imperfect, solution. Thirdly, and perhaps most tangibly, the IT Monitoring Tool literally draws upon the TKDL as a source of data.
Given this larger context, the TKDL and the IT Monitoring Tool present less as isolated, individual projects and more as different facets of a techno-legal knowledge infrastructure that has been developing within and across the Indian central government over the last twenty years. While the TKDL is an early, if not the earliest, component of this larger knowledge infrastructure, the IT Monitoring Tool presents as its most recent facet. While the purpose behind this knowledge infrastructure shifts and expands over time it has, to date, remained primarily oriented around distinguishing between the legitimate use of Indian bio-cultural patrimony (bioprospecting) and the illegitimate appropriation of these resources (biopiracy). However, a near-future expanded use anticipates that these tools will soon be capable of not only distinguishing between bioprospecting and biopiracy, but will also be able to trace the location, monitor the scale, and measure the results of these activities.
When taken together as part and parcel of an emergent phenomena, it is clear that over the course of their individual project lives the TKDL and the IT Monitoring Tool have both changed. For example, the TKDL expanded at different points in time to include new ethno-medical systems deemed to be under threat of piracy, such as yoga in 2008 and Sowa Rigpa sometime around 2017 or 2018.[41] Additionally, there has been a continued, if never quite realised, discussion to use the TKDL as a platform for commercial and non-commercial scientific research and development. Similarly, the IT Monitoring Tool, which has not yet been released, will be subject to and must respond to similar fluctuations. As such, we would like to move from looking at the history informing the IT Monitoring Tool and turn to consider its future impact and efficacy.
B. The Future of the IT Monitoring Tool
One of the goals of the Indian government is to produce a classificatory system that distinguishes the legitimate use of genetic resources, bioprospecting, from those involving the illegitimate use of genetic resources, biopiracy. Creators of the IT Monitoring Tool have suggested that, when fully scaled up and comprehensively trained, the tool can be used for more than simply monitoring bioprospecting activities and flagging suspected instances of biopiracy for review.[42] In addition, the creators believe that the IT Monitoring Tool will have the capacity to generate reports about where, when, and how Indian genetic resources are used around the world, who is involved in this research, and how the benefits that flow from this work are distributed. There is also a possibility that this may eventually lead to more precise information about the use of genetic resources between countries, particularly between developed and developing countries, and how foreign researchers are collaborating with or involving their Indian counterparts. If done well, this could be an important tool for understanding how biodiversity research is taking shape, how the benefits that flow from this work are being distributed, as well as generating scientific insights more broadly. However, if done poorly, such statistics and visualisations can be vectors of misinformation that, once produced, are opaque, unregulated and difficult to contest.[43]
Additionally, the IT Monitoring Tool, like the TKDL, has begun to move beyond South Asia to influence other countries throughout the world and is increasingly discussed as an exemplar of global best practice regarding the implementation of the Nagoya Protocol.[44] For example, the tool has been the subject of discussions at the United Nations and will be highlighted at the Convention of Biological Diversity’s Committee of Parties meeting in China during 2021.[45] A reason for this is that the IT Monitoring Tool offers both a means to monitor compliance within India, as well as the potential to monitor compliance globally. In doing so, the IT Monitoring Tool holds promise for regulating the way Indian genetic resources are used outside of India. As a result, the IT Monitoring Tool may address one of the most difficult problems facing the regulation of genetic resources; namely, that little can be done once resources have moved outside of a jurisdiction. A primary innovation of the TKDL was to recognise this problem and attempt to provide a mechanism to resolve the underlying issues. The TKDL did this by directly providing patent examiners in participating jurisdictions with the evidence required to challenge and revoke patents that had been inappropriately granted over Indian genetic resources. While this marked a step-change in how genetic resources are regulated, the TKDL approach still faced a number of shortcomings. One of which is that the project has not been able to achieve a global impact since only a few jurisdictions have struck agreements to use the TKDL as a resource in patent examination processes. Secondly, in order to operate effectively, individual patent examiners in participating jurisdiction must accept the TKDL resource, understand when to access it, and how to apply the evidence to claims under their review. At this stage, such facility of patent examiners is unclear and some commentators have been critical of its implementation in participating jurisdictions. While the IT Monitoring Tool may address some TKDL shortcomings, this is not guaranteed as the system has not been fully implemented and may face additional hurdles.
The IT Monitoring Tool also marks a further innovation in the regulation of genetic resources which is linked to the unique way in which the Nagoya Protocol operates. As noted earlier, the Nagoya Protocol not only applies within the countries where it is enacted, but it also functions to control resources that are imported into Nagoya compliant countries (even though the use may originate in a country that has not adopted Nagoya). As a result, the reach of Nagoya extends beyond the countries where it has been introduced into local law. Additionally, a growing number of non-state actors – universities, journals, and funding bodies have made, or are considering making, Nagoya-compliance a precondition for working with them. The upshot of this is that non-compliance with Nagoya carries global consequences. In the context of the IT Monitoring Tool, this means that if India were to identify a non-compliant use of a Nagoya protected resource and issue a public notice of non-compliance, then there would be a much greater possibility that this would carry consequences even if the misuse occurred outside of India. Flagging such non-compliant uses should, in theory at least, mean that products based on tainted genetic resources would not be eligible for import into any of the 129 countries that have ratified Nagoya. This would also, in theory, apply to any non-state actors who have elected to comply with the conditions of the Nagoya Protocol. Further, this might give venture capitalists cause to pause and consider whether they should invest in products built on a tainted use.
Despite such potential, there are many unknowns. As the scheme requires the Indian state to develop an effective means of publicising non-compliance and for foreign agencies to act on any such notice, the effectiveness of the scheme will depend on how willing and able foreign customs agents and border authorities are to check and enforce the Nagoya-compliance of materials and products that enter into their jurisdictions. This will hinge, in part, on how entrenched the demand for Nagoya compliance becomes outside of those countries that have implemented Nagoya into their domestic law. The effectiveness of the IT Monitoring Tool will also depend on the tool’s ability to identify Indian-protected genetic resources. For this to occur, the IT Monitoring Tool will need to be able to differentiate Indian genetic resources that fall within the scope of Nagoya and those Indian genetic resources that have been specifically excluded from its reach.[46] Inconsistent approaches as to how these exceptions are determined in different countries will make this a difficult task. In addition, the IT Monitoring Tool will need to differentiate between situations where someone uses a plant of Indian-origin within India, which will be governed by Indian access and benefit sharing laws, from the situation where someone uses a plant of Indian-origin outside of India, which falls outside the reach of Indian law.
The effectiveness of the IT Monitoring Tool also depends on the genetic resources being named consistently across the different digital repositories. The problem here is that despite the apparent stability of taxonomic and nomenclatural descriptors, as Geoff Bowker has demonstrated, these systems of scientific naming and ordering do change over time, often in response to contemporaneous developments in available information technology and the professional re-organisation of a scientific discipline.[47] Given the recent computational turn in the biological sciences, the consequential re-organisation of the profession that this has triggered, and the growing discussions about the legal status of genetic information (or digital sequence information) under the Nagoya Protocol, it will be interesting to see what impact this has on the future configuration and use of the IT Monitoring Tool. One of the lessons we can take from the TKDL and the IT Monitoring Tool is that rather than seeing this as creating a problematic gap between law and science, that this is better seen as the latest iteration of an evolving and constantly changing techno-legal knowledge infrastructure that needs to be understood in processual terms; as emergent phenomena that are always in-the-making and that rarely, if ever, stand still or present as finished projects capable of fully realising their objectives. By seeing the IT Monitoring Tool (and the TKDL) in this context, we gain a more nuanced understanding of how law and technology have come together in India to regulate bioprospecting and biopiracy.
V. Conclusion
The Indian central government’s Nagoya compliance monitoring system offers important lessons for information regulation law and theory. Firstly, the government’s approach to using law and technology to interpret and implement the state’s obligations under the Nagoya Protocol reminds us that information systems are rarely, if ever, created de novo. Rather they are composed of a mixture of heritage and new constructs. In this sense, the IT Monitoring Tool, and the legal and technological complex upon which it operates, provides us with a deeper understanding of the influence of pre-existing information infrastructures. In this sense, this case study demonstrates that these pre-existing information infrastructures need not be exclusively technical or physical constructs, but may also include legal, policy, social, economic, and ethical constraints as well.[48] Further, when influential infrastructural constraints include legal requirements, as with India’s IT Monitoring Tool, the information system becomes an important site for understanding how laws, subject to interpretive flexibility, are enacted on the ground.
Secondly, at a more general level, the Nagoya compliance monitoring system offers us with an insight into a mode of regulation where the legal-regulatory apparatus is embedded within the information system itself. That is, it is an example of a situation where the information system has become a tool, rather than an object, of legal regulation. It is through this configuration of the relationship between law and technology that the IT Monitoring Tool escapes the dominant discourse of temporal mismatch. Instead, the IT Monitoring Tool is a legible example in which the interpretation of legal forms and technological infrastructures are entangled projects that are shaped, in part, by larger societal concerns. In this sense the Nagoya Protocol emerges as an unusual example of legal compliance through design.[49] To date, most of the literature on ‘legal compliance through design’ focuses on the areas of FinTech, business process regulation and compliance issues, and privacy. What makes the Indian approach to the Nagoya Protocol a particularly interesting example of this techno-legal approach is that is being deployed by a nation-state to track international laws around access and benefit sharing pertaining to genetic resources.
Finally, in so far as the IT Monitoring Tool represents one of the latest and in some ways the most complete example of legal compliance through design, it acts as a harbinger of things to come. It also provides insights into how to think about these new techno-legal modes of regulation and the tools, social processes, and political values with which they are linked. In this sense we can draw lessons from the work of Chris Kelty[50] and Gabriella Coleman[51] and, more recently, by Lyria Bennett Moses and Monika Zlanieriute who posit that information technologies, modern democratic principles, and regulatory structures are always-already entangled within one another.[52] In describing this relationship, Kelty and Coleman examine how political, moral, and aesthetic social projects are bound up with the development of open source coding communities and the work they collectively undertake. Similarly, Bennett Moses and Zalnieriute focus on the idea that information technologies and the law are both, inextricably, social projects that are shaped in response to past events and influenced by future aspirations and imaginaries.[53] In this sense, a detailed understanding of the Indian state’s use of technology to implement its obligations under the Nagoya Protocol can be understood as an effort through which national agencies pragmatically blend limited human and financial resources to harness machine learning capabilities and match these against existing informational resources. In doing so, the creators of the IT Monitoring Tool are crafting a national project through which the nation understands its past relationship to genetic resources and the possible opportunities that such resources might offer for the future.
- Roger Brownsword, Eloise Scotford and Karen Yeung, ‘Law, Regulation and Technology: The Field, Frame and Focal Questions’ in Roger Brownsword, Eloise Scotford and Karen Yeung (eds), The Oxford Handbook of Law, Regulation and Technology, (Oxford University Press, 2017) 3, 3–4. ↵
- See Lawrence Lessig, Free Culture: How big media uses technology and the law to lock down culture (Penguin Press 2004) for a classical and powerful discussion on this gap, or mismatch, between the slow temporality of time and the rapid advance of technological development. ↵
- See Lyria Bennett Moses and Monika Zalnieriute ‘Law and Technology in the Dimension of Time’ in Sofia Ranchordas and Yaniv Roznai (eds.), Time, Law and Change: An Interdisciplinary Study, (Hart Publishing 2020). ↵
- Pompeu Casanovas, Jorge Gonzalez-Conejero, Louis de Koker, ‘Legal Compliance by Design (LCbD) and through Design (LCtD): Preliminary Survey’ (2018) Proceedings of the 1st Workshop on Technologies for Regulatory Compliance, 33-49. Compliance through design’ is an approach that recognizes there is an element of choice in the way that public and private entities interpret and action legal rules. Furthermore, this choice may be affected by policy requirements, business objectives, appetite for risk, or other factors unique to a social context or institution. Bennett Moses and Zlanieriute (n 3). ↵
- ‘Genetic resources’ includes plants, animals, and microorganisms. ↵
- Daniel Robinson, Biodiversity, access and benefit-sharing: Global case studies (Routledge Press 2015). ↵
- The Nagoya Protocol on Access to Genetic Resources and the Fair and Equitable Sharing of Benefits Arising from Their Utilization to the Convention on Biological Diversity <https://www.cbd.int/abs/doc/protocol/nagoya-protocol-en.pdf> ↵
- Kanchana Kariyawasam and Matthew Tsai, ‘Access to genetic resources and benefit sharing implications of Nagoya Protocol on providers and users’ (2018) Journal of World Intellectual Property 289–305; Jorge Cabrera Medaglia, Frederic Perron-Welch, and Freedom-Kai Phillips, Overview of national and regional measures on access and benefit sharing challenges and opportunities in implementing the Nagoya Protocol (3rd edn, CISDL Biodiversity and Biosafety Law Research Programme 2014); Elisa Morgera, Elsa Tsioumani, and Matthias Buck, Unravelling the Nagoya Protocol: A commentary on the Nagoya Protocol on Access and Benefit-sharing to the Convention on Biological Diversity (Brill 2014). ↵
- Tom Dedeurwaerdere, Paolo Melindi-Ghidi, and Arianna Broggiato, ‘Global scientific research commons under the Nagoya Protocol: Towards a collaborative economy model for the sharing of basic research assets’ (2016) 55 Environ Sci Policy 1. ↵
- Brad Sherman and Robert Henry, ‘The Nagoya Protocol and historical collections of plants’ (2020) Nature 430; E. Marden et al, ‘Sharing and reporting benefits from biodiversity research’ (2020) 30(5) Molecular Ecology 1103. ↵
- Ibid. ↵
- The Nagoya Protocol on Access to Genetic Resource’s and the Fair and Equitable Sharing of Benefits Arising from their Utilization to the Convention on Biological Diversity 2014, Art 14. ↵
- There is an additional indicator that tracks the circulation of the genetic resources across the global value chain known as the ‘Check Point Communique’. However, this mechanism has not been widely utilized at this time and will not be discussed within this paper. ↵
- Each Party to the Nagoya Protocol can designate one National Publishing Authority. Once domestic permissions have been obtained the National Publishing Authority can log into their account on the clearing house and publish an IRCC to this effect. In addition to National Publishing Authority, Indigenous Peoples and Local Communities can also obtain an account to upload supporting information onto the clearing house website such as community protocols and customary laws for accessing traditional knowledge associated with the genetic resources being utilized. However, Indigenous Peoples and Local Communities cannot publish IRCCs. See CBD Guide to the Access and Benefit Sharing Clearinghouse <https://www.cbd.int/abs/en/ABSCHGuide.pdf> accessed 9 Feb 2021. ↵
- CBD Access and Benefit Sharing Clearing House: Countries <https://absch.cbd.int/countries> accessed 9 Feb 2021. France, the state with the next highest numbers of certificates had filed 353. ↵
- Kevin E Davis, Benedict Kingsbury, and Sally Engle Merry, ‘Indicators as a Technology of Global Governance’ in International Law and Justice (Working Papers, NYU School of Law 2011); Sally Engle Merry, Seductions of Quantification: Measuring Human Rights, Gender Violence and Sex Trafficking (Uni of Chicago Press 2016). ↵
- International Union for Conservation of Nature (IUCN), ‘Countries: India’ <https://www.iucn.org/asia/countries/india> accessed 9 Feb 2021. ↵
- At the national level, environmental protection is located in Articles 48A and 51A(g) of the Constitution of India and enabled through numerous wide-ranging policies, programmes, and projects that cover the management of ex-situ and in-situ genetic resource collections. ↵
- India signed the CBD on 5 June 1992 and ratified it on 18 Feb 1994. ↵
- Intellectual Property Watch (2012), ‘India Ratifies Nagoya Protocol on Biodiversity Access and Benefit-Sharing’ <https://www.ip-watch.org/2012/10/05/india-ratifies-nagoya-protocol-on-biodiversity-access-and-benefit-sharing/> accessed 9 Feb 2021. ↵
- NBA functions include issuing central guidelines on access and benefit sharing requirements and procedures, granting official approvals for access, advising both central and state governments, and contesting intellectual property claims on any Nagoya-protected resources that are lodged in foreign jurisdictions. ↵
- State Biodiversity Boards receives applications that have been duly filed with the NBA and acts as mediator with the appropriate local committee in negotiating and monitoring resource access and benefit-sharing. In doing so, the state boards can form expert committees to assist in the review of the matter. Once a state board has been satisfied that an appropriate access and benefit sharing agreement has been struck, then it sends this on to the NBA for further processing. See National Biodiversity Authority, Operational Guidelines to the State Biodiversity Boards for Processing of Applications for Access to Biological Resources’ (2019). ↵
- As of early Feb 2020 more than 242,000 Biodiversity Management Committees have been organized to represent grass-roots level interests. BMCs are authorized under Section 41 of the Biodiversity Act, 2002 and are responsible for developing People’s Biodiversity Registers in consultation with local communities on Nagoya-protected resources and to track access and benefit sharing agreements. These registers have been subject to recent criticism for pitting state, NGO, university, and local communities interests against one another, see Bahar Dutt ‘The Peoples’ Biodiversity Register, Meant to Empower Local Communities is Leaving Them Out’ The Hindu (18 Oct 2020). ↵
- The State Biodiversity Boards are responsible for permits by domestic entities for domestic research and commercialization purposes. The state boards also coordinate with the local committees to establish an access and benefit sharing agreement. ↵
- Additionally, there are numerous legislative, administrative and policy measures for which the NBA is responsible and which empower the Authority to act. For example, India’s Biological Diversity Act 2002 provides in Art 6(1) that patent applicants using Nagoya-protected resources from India must obtain the permission of the NBA before making their claim in any jurisdiction. Additionally, Art 6(2) gives the NBA the right to impose a benefit-sharing obligation or royalty fee related to any financial benefits arising out of the commercial utilisation of such rights. ↵
- Vinod Mathur, ‘ABS-IT Monitoring tool: Relevance of Access and Benefit Sharing in India’, presentation at the Webinar on IT Tool for Monitoring Access and Benefit Sharing in India (United Nations Development Program’s Global Access and Benefit Sharing Project 12 Feb 2020) <https://vimeo.com/417263942> accessed 9 Feb 2021. ↵
- In some instances, resource access will require agreements with multiple local committees. See National Biodiversity Authority, Operational Guidelines to the State Biodiversity Boards for Processing of Applications for Access to Biological Resources’ (2019). ↵
- Ibid. ↵
- The United Nations has six official languages including; Arabic, Mandarin Chinese, English, French, Russian and Spanish. According to clearing house guidelines IRCCs should be published in one or more of these to ensure legibility. The Indian approach is to publish IRCCs in all six languages. ↵
- Shalini Bhutani and Kanchi Kohli, ‘Despite Landmark Judgment, Issues of Regulation Remain in India's Biodiversity Regime’ (5 March 2019) The Wire <https://thewire.in/law/divya-pharmacy-india-biodiversity-act> accessed 9 Feb 2021; Lakshmi Supriya, ‘How Laws to Protect Biodiversity Backfired on Scientists Trying to Save It’ (26 July 2018) The Wire <https://thewire.in/the-sciences/how-laws-to-protect-biodiversity-backfired-on-scientists-trying-to-save-it> accessed 9 Feb 2021. ↵
- Dr. Mathur said that he has ‘no problem saying that once in a while that patents are filed without taking proper permissions’; a sentiment that Dr. Aeshita Mukherjee believes was a significant understatement. ↵
- Aeshita Mukherjee, ‘Global Capacity Building Workshop on the Monitoring and Utilization of Genetic Resources Under the Nagoya Protocol’ (30 Sept – 2 Oct 2019, Germany). While there is a domestic law within India requiring foreign patent applicants to obtain permissions from the NBA, practically speaking the Authority has no jurisdiction. ↵
- As Dr. Vijay Kumar of Chennai’s Centre for Advanced Computing and Dr. Paul Odlham of One World Analytics said, this is simply a problem of scale. ↵
- In analysing framing knowledge infrastructures it is important to trace the context from which they emerge, identify which parties contribute to its fabrication, examine how they are sustained and maintained, and note the wider political opportunities and challenges that are associated with their development. See Helena Karasti, Florence Millerand, Christine M. Hine and Geoffrey C Bowker, ‘Knowledge Infrastructures: Part 1’ (2016) 29(1) Science and Technology Studies 2. ↵
- On a related matter see Paul Rabinow, French DNA: Trouble in Purgatory (Uni of Chicago Press 1999). ↵
- Presented by Aeshita Mukherjee at the ‘Global Capacity Building Workshop on the Monitoring and Utilization of Genetic Resources Under the Nagoya Protocol’ (30 Sept – 2 Oct 2019, Germany). ↵
- See Alfred North Whitehead, Process and Reality (Free Press 1978); Alfred North Whitehead, Science and the Modern World (Free Association Books 1985). ↵
- Allison Fish, ‘The Commodification and Exchange of Knowledge in the Case of Transnational Yoga’ (2006) International Journal of Cultural Property 189-206. ↵
- Allison Fish, ‘Authorizing Yoga: The pragmatics of cultural stewardship in the digital era’ (2014) 8(4) East Asian Science, Technology, and Society 439. ↵
- Fish, ibid. ↵
- See “Major Milestones” page of the Traditional Knowledge Digital Library website, available at <http://tkdl.res.in/tkdl/LangGerman/Common/milestones.asp?GL=Eng> (visited on 25 June 2021). The initiation of digitsation activities related to yoga began on January 2008. There is no specific date listed for initiation of activities in relation to Sowa Rigpa, however, the CSIR-TKDL Unit did recruit various positions to work on the Sowa Rigpa portion of the TKDL in early 2018. ↵
- Presentation by Dr Paul Oldham at ‘Global Capacity Building Workshop on the Monitoring and Utilisation of Genetic Resources Under the Nagoya Protocol’ (30 Sept – 2 Oct 2019, Germany). ↵
- See C O’Neil, Weapons of Math Destruction (Crown Books 2016) for a discussion of the difficulties and dangers inherent in algorithmic decision-making. While O’Neil references socio-political examples and the IT Monitoring Tool purportedly draws its data from research in the natural sciences, a similar argument might apply here in understanding how the reporting function of the tool might operate. ↵
- This is also something that happened with respect to the TKDL. The format for the TKDL has been adopted by countries and Indigenous communities throughout the world to varying degrees. For example, IP Australia both uses the TKDL in their review of patent applications and is considering building something similar for Australian Indigenous communities. Additionally, Australian Indigenous communities are considering their own databasing projects to protect language and ethnobotanical knowledge. ↵
- This meeting was to take place in 2020, but was delayed due to the COVID-19 pandemic. ↵
- For a critical discussion of these issues see Prashant Reddy Thikkavarapu, ‘Access to Plant Genetic Resources and Benefit Sharing: Has India Lost the Plot?’ (2018) 3 Intellectual Property Quarterly 181. ↵
- Gregory C Bowker, ‘The Game of the Name: Nomenclatural Instability in the History of Botanical Informatics’ in Proceedings of the 1998 Conference on the History and Heritage of Science Information System (Asis Monograph Series, 1998). ↵
- Karasti et al (n 37). ↵
- Pompeu Casanovas, Jorge Gonzalez-Conejero, Louis de Koker, ‘Legal Compliance by Design (LCbD) and through Design (LCtD): Preliminary Survey’ (2018) Proceedings of the 1st Workshop on Technologies for Regulatory Compliance, 33-49. ↵
- Chris Kelty Two Bits: The Cultural Significance of Free Software (Duke University Press 2008). ↵
- Gabriella Coleman Coding Freedom: The ethics and aesthetics of hacking (Princeton University Press 2013). ↵
- Bennett Moses and Zlanieriute (n 3). ↵
- Bennett Moses and Zlanieriute, ibid. ↵